01 What is Access Control

Introduction
Consumers interact with electronic access control systems every day through keyless entry and smart home technology. The first thing that comes to mind is often the remote key, keypad, or key card used to enter an office, car, or home. However, there is a lot more to access control than a FOB and a card reader at the entrance of a door.
The behind the scenes technology determines which electronic access control system is the best application for the area. A commercial-grade access control system provides the initial classification of who gets into the facility and who doesn’t, along with a second level of security, controlling who has access what areas of the establishment down to each file cabinet or drawer containing sensitive information. Sophisticated systems can differentiate access by user, track activity, and provide security logs for administrators. Some systems communicate and coordinate with other security measures for a streamlined and integrated approach to protecting the company, its employees, its assets, and its data.
“There is no doubt that access control technology is progressing and evolving at the fastest pace ever in the security industry. And the need for enhanced security due to new sources of threats, increased liability, and even mandated compliance has made more funds available to public and private entities to enhance security. As a result, more and more money has been allocated in recent years to help keep unwanted people from entering facilities.”
– Security Magazine, in June 2019, reports
The following information outlines the components and operation protocols of electronic access control systems, the moving parts necessary for seamless implementation, features that can substantially increase security levels, and where to use which systems to optimize efficiency.
What are Electronic Access Control Systems?
What are Electronic Access Control Systems?
Access control systems restrict entrance to secure areas of a property, building, room, file cabinet, drawer, or other area containing sensitive or proprietary information, assets, or data. The automated nature of the system provides 24/7 protection along with 24/7 access. As the front line of defense, companies use locks combined with log-in credentials to enhance traditional security measures. Any space requiring limited access to authorized personnel only should have an access control system in place.
Businesses today want to do more than simply restrict entry. They want to monitor and manage access. Increased security and monitoring require more than a deadbolt and keyless lock. It requires an access management system. One that controls who may enter, where they may go, and when they have permission to be in a secure location.

Computer-based electronic access control systems marry the needs of physical security with the capabilities of information security. With the use of credentials such as codes, FOB, key cards, or biometrics, systems have the capability to provide quick and convenient access to authorized personnel, while tracking and monitoring the movement of those who enter. New technologies have rapidly increased not only the ability to restrict access to secure areas, but also the ability to monitor and manage that access through electronic means to better protect assets and data.
Users gain entry after the system verifies the credentials presented. The software tells the system when to unlock the door, records the event, and can relax the area to maintain security. In the event of credential failure, the system records the failure and might activate back up security, such as video cameras, alarms, or electronic notifications. Attempts of forcible entry will also record the breach and activate an alarm.
Security Information Watch in an industry report stated, “The advancements being made in mobile technologies, cloud technologies, Artificial Intelligence (AI), biometrics on mobile devices, and wearables, access control is now more integrated with what is considered “state of the art” technology than ever before.” ²
There is a very significant amount of innovation and new products that are fundamentally shifting how access control is delivered and utilized.” ³
Why Companies Choose Access Control Systems
Compliance
Many industries require businesses to meet compliance standards, send reports to government agencies, and maintain policies and procedures to ensure all operations meet the laws and standards for the industry.
Compliance requirements often include protecting assets and client data. Industries impacted by extensive compliance requirements include healthcare, financial services, data centers, and SaaS providers.
Reduce Internal Theft
For many businesses, internal theft significantly impacts the bottom line. Access control systems create checks and balances by tracking the entry and exit to secure areas. Monitored systems can reduce losses, catch
incidents of internal theft, and provide evidence for the prosecution.
“In most cases, the client is implementing high security to comply with government regulations. For instance, Dept. of Defense contractors usually have to comply with UL2050 requirements or meet the security needs of their clients. Drug companies often have to comply with the Drug Enforcement Agency requirements for access to controlled substances. In most cases, the government regulations will dictate the types of security systems that can be used for these requirements.”⁴
Secure Sensitive Data and Assets
Any company handling or processing sensitive data, intellectual property, or valuable assets require additional measures to ensure the safety and security of the information and assets under stewardship.
Gather and Use Data to Improve Operations
Monitoring through an electronic access control system increases the ability to identify vulnerabilities in current policies and procedures. Managers and administrators can then make positive changes to existing processes to reduce the risk of loss.
How Access Control Systems Operate
An access control system includes the following steps:
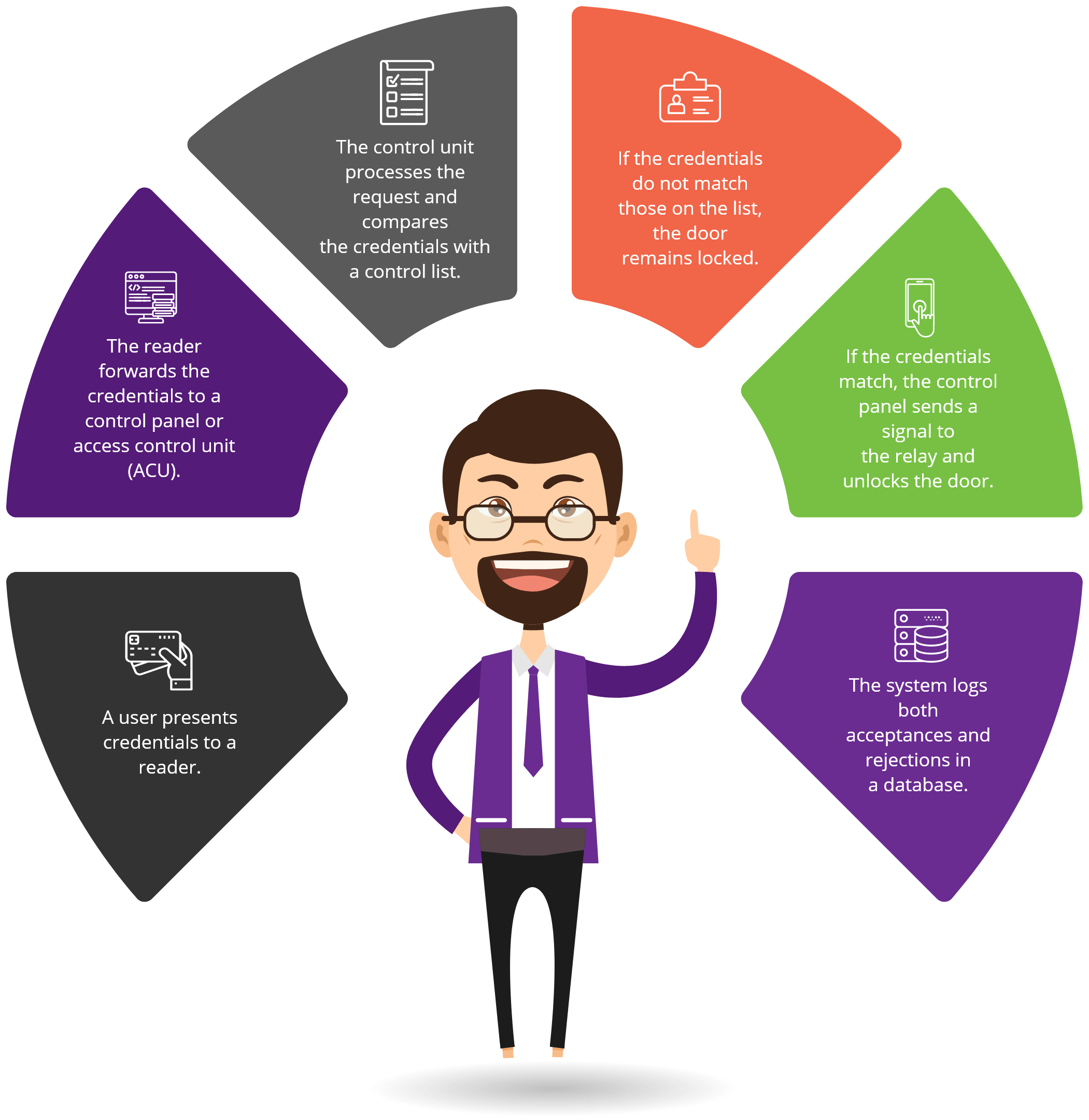
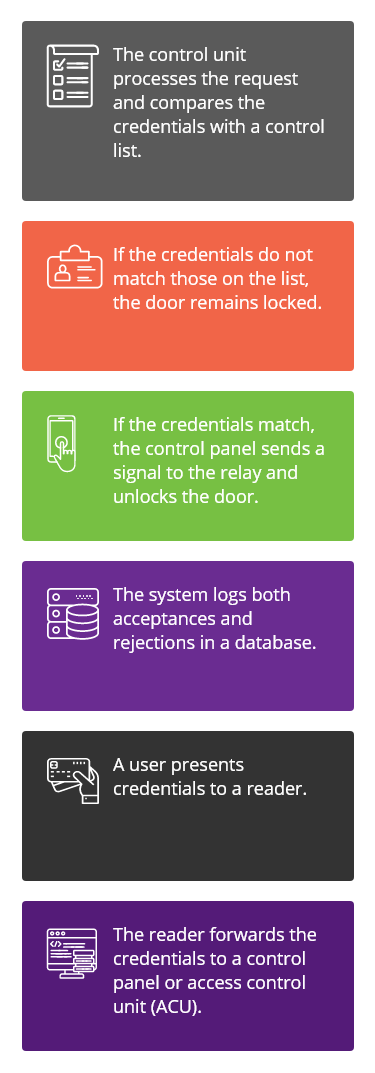
There are Three Key Elements to the Operations Process
The User Facing Experience
The Administration Facing Experience
The Infrastructure

The User Facing Experience includes an access card, the card reader, and the control panel. Most people are familiar with key cards, ID badges, and other forms of security credentials. The user presents the access code and the system approves or rejects the request for entry. Access cards can include a keypad, bio-metric, a swipe, tap, or a proximity card. Proximity cards operate when the user is within a short distance, typically two to six inches, from the reader. Proximity readers can communicate with an ID badge, FOB, key, card, or smartphone. Access management control systems record the activity, once the user activates the reader to verify credentials. “Innovations are having a profound effect on the user experience. Where security may have been seen as a barrier or a hindrance in the past, it is now enabling a truly seamless experience.” ⁵

The Administration Facing Experience typically includes a management dashboard or portal where the administrator, manager, security, or IT personnel will gain access to the system. The dashboard allows authorized personnel to add or delete users, change user credentials, set the parameters for entry to the secure area, and decide who will have access to what areas under which circumstances. The dashboard often uses cloud storage, giving administrators the ability to access the system from anywhere. Programmers can automate certain processes and reports and connect them to other systems within the company. For example, a programmer could design the system to add user credentials during the on boarding process and delete credentials upon termination. While most of the administrative side of access control involves automated processes through software, the system does require a manual entry when adding, changing, or terminating access.

The infrastructure of the system includes the locking device, the access control panel, cables, and the server. Electronic locking systems may continue to use a deadbolt to secure entry to interior and exterior doors. File cabinets, desks, and other access points frequently use E-locks. For example, Senseon offers both side-mounted and under-mounted E-locks, which can secure any desk or cabinet door or drawer will 250 pounds of brake force, without requiring a bulky deadbolt lock.
Fail-Safe Versus Fail Secure Systems
Along with force securing a locking system, each system functions as a fail-safe or fail-secure locking device.
A Fail-Safe
A Fail-Safe lock remains unlocked until an electrical current activates the lock. The power requirement creates a system vulnerability because natural disasters,
storms, or sabotage can create a power failure, leaving an area unsecured.
Fail Secure
Fail-Secure systems require electrical power to release the access control system. Even in the event of a power failure, the system remains intact, maintaining
security until the restoration of power, or a system override releases the lock. Fail-secure locks offer the highest level of security available. The level of security needed, items secured, fire codes, and compliance regulations impact which system works best in the given application.
The Server
The server stores credentials in a database. When a user requests entry, the system compares the presented credentials with the database.
The best access control systems allow real-time changes to the database. For instance, upon termination, an employee will immediately cease to have access to a secure area, and a new hire will instantly gain access to approved locations.
Servers can be dedicated to a particular lock or part of a larger system. Windows or iOS-based programs that include cloud storage allow management or administrators to make changes to the database through any secure internet connection.
The most sophisticated servers track activity in any secure zone and document when someone enters or leaves the area with a time and date stamp, logging each entry and exit to an individual. Logs allow a manager, IT personnel, or security to view activity at a specific location over a particular timeframe. Standalone units typically store credentials at the reader rather on a centralized control panel. Administrators can access the database at the reader or through an app.
02 Types Of Access Control
Electromechanical Locks VS Electromagnetic Locks
Technological advancements have removed dependence on conventional lock and pin tumbler systems, making way for a more secure, flexible, and affordable way to protect everything from buildings to individual drawers and doors in an office or home.

The Basics
Electromechanical (E-Locks)
Consists of:
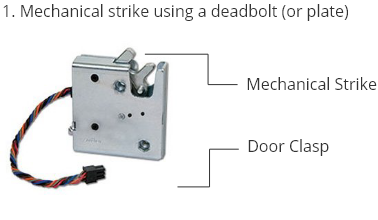
The mechanical strike will secure the lock
and hold the deadbolt (or plate) in place.
Electromagnetic (Mag-Locks)
Consists of:

An electrical current will pass through the
electromagnetic plate, causing a magnetic
force to attract and hold the armature plate
in place.
Key Benefits
Fail-secure & Fail-safe Locks
Fail-Secure Locks
Requires power to release the lock. In the event of a power failure, the door/drawer remains locked until someone activates an override.
Fail-Safe Locks
Requires power to remain active. A Loss of power will unlock door/drawer causing application to remain unsecured until the power comes back online.
Modern Access Control Systems
Locking Devices For Cabinets & Drawers Can Provide:
Standalone Locking Systems Versus Integrated Systems
Standalone Locking Systems
Standalone access controls are independent and do not communicate with other security networks within an office or building. Integrated access control, on the other hand, can communicate with existing systems to create a comprehensive security network for the entire building or
complex. In some cases, the integration will include compatibility with the software used by other departments such as HR.
Integrated Systems
The key benefit of integrated systems is that everything works together for a more seamless user experience. The downside is that it can be more expensive to install and operate because it requires software that can communicate with multiple systems.
It is common to integrate security systems to coordinate access control measures with video surveillance, intruder alarms, perimeter security, or fire detection systems. Having all elements of security working in tandem improves the efficiency of the system, reduces redundancy, and streamlines implementation.
Essential Components of an Electronic Access Control System
Essential Components of an Electronic Access Control System
The term access control often brings images of vaults, secure elevators, and buildings. However, today’s access control also includes rooms, workstations, file cabinets, desk drawers, along with equipment like printers or computers.
A typical system has two major components: One controlling the access to a physical location and a system verifying the presence of authorized personnel. The electronic access controlling the physical location, such as a door, typically contains several elements: The lock, the reader, a control panel to authenticate the credentials, along with access control hardware and software.
Presenting Credentials
Single or Multi-factor Verification
Contactless cards

Users carry credentials on access cards, key cards, ID badges, or an app on a smartphone. The user presents credentials at an access control point, which could be an exterior or interior door to a building or office, a gate (such as in a parking garage or gated community), an elevator, a turnstile, cabinet doors, and drawers, or other barriers to entry. The lock secures the door by electronic means, which could be a stand-alone unit operated with a switch or level or part of a bigger system. Credentials involve a tangible or physical object or action. Something the individual has (a keycard or access badge), something they know (a passcode or PIN), or something they are (a biometric measure such as fingerprint or eye scan), or a combination of these.

Systems will require either single or multiple factor verification. Multiple factor verification requires authentication of two or more sets of credentials before the system will authorize entry. For instance, an individual might need to present both a key card and a password. Two-factor verification is the most common way to add an additional layer of security. Another level of security requires credentials from two different individuals rather than two forms of identification from one individual. Duel authentication can prevent internal security breaches.

Contactless cards use near field communication⁶ to connect the device holding credentials with the reader. Technology includes radio frequency identification (RFID), QR codes, Wi-Fi, or Bluetooth. With near field communication, users can unlock a door or drawer once they are within two to six inches of the reader, without touching the device.
Credential Readers and Control Panels
A reader can be a keypad with code entry, a card reader using a FOB, key card, or smart device, or a biometric reader verifying the credentials through the individual’s biometrics. The reader communicates with a control panel, which will
verify the credentials presented against an approved access list. The approval process involves communication between the reader and a host, server, or control panel. A central control system can operate from a computer as opposed to a reader at the site of the lock. Access control readers are classified by function: There are basic readers, semi-intelligent readers, and intelligent readers. Each offers different levels of functionality.
Basic Readers without Intelligent Capacities
The reader and control panel is at the point of entry. Credentials typically involve a PIN, passcode, or biometric identification such as a fingerprint entered on a keypad. A basic reader provides the lowest level of security and only comes as a standalone device.
Semi-Intelligent Readers
Semi-intelligent readers include the lock and contact needed to control the door hardware but does n ...
Semi-intelligent readers include the lock and contact needed to control the door hardware but does not make access decisions. The reader and control panel is at the point of entry. When an individual presents credentials, the reader communicates with the main controller and unlocks the door if the credentials match the approved access list. Administrators can make changes to credentials at the reader or remotely depending on the system. To operate the unit must have an active connection to the main controller. Semi-intelligent readers can connect to multiple locks using the same reader or portal. Provides a high level of security but cannot integrate with other security systems and is only available as a stand-alone device.
Intelligent Readers
Intelligent readers possess the inputs and outputs necessary to control door hardware along with the ...
Intelligent readers possess the inputs and outputs necessary to control door hardware along with the memory and processing power to independently make access decisions. Intelligent readers have the most flexibility and can work as an independent unit or in conjunction with other security measures. Managers can control entry remotely, track entrance and exits using a tracking log, and operate multiple locks and points of entry from the same control panel. Used in settings where access control is an integral part of operational security and the need for additional tracking features exists.
Use of Sub-Controllers
Both semi-intelligent and intelligent readers have the capability of controlling multiple locks. Eac ...
Both semi-intelligent and intelligent readers have the capability of controlling multiple locks. Each reader connects to a sub-controller, which then connects to the central control panel. The sub-controller forwards access credentials to the main server to authenticate credentials and unlock a door, drawer, or cabinet. The use of sub-controllers can reduce the load on the main controller and lower the overall cost of securing an area. For example, if an office has 15 file cabinets or desk drawers containing secure information, a single system could connect all the drawers to the same main controller through sub-controllers.
Integrated Control Access Systems using main Controllers and Intelligent Readers.
In this case, the door or drawer hardware connects directly to either a semi-intelligent or intellig ...
In this case, the door or drawer hardware connects directly to either a semi-intelligent or intelligent reader. The reader could forward credentials to the main controller or contain an internal database. The reader can approve credentials and record events if an issue arises with the connection to the main controller. Most intelligent readers have internal databases where most semi-intelligent readers do not.
Main Controllers Connected to a Network
Main controllers connected to a network operating in much the same way as integrated control access ...
Main controllers connected to a network operating in much the same way as integrated control access systems. The key advantage is speed and tracking. The network interface transmits data quickly, allows remote changes to the credentials. Computer-based systems are responsive and work in tandem with other security measures such as video surveillance or alarms. Network integration adds important features used by larger organizations. For instance, systems can use the existing infrastructure without the need to install new lines of communication through software programs. Network access control systems give administrators more control, more oversight capabilities, can accommodate a higher number of users, and offer remote troubleshooting. The controller can initiate an alarm to the host PC and at the reader location, in the event of failed credentials or attempted forced entry. It is also possible to coordinate the system across multiple locations separated by distance. The downside is that network connections increase vulnerability to cyber security breaches, which can compromise both credentials and the data secured within the system. Heavy internet traffic can also cause delays in communication between the main controller and the reader.
Types of Electronic Access Control Management Systems
Electronic locking systems consist of either keypad, Key FOBs, or remote access locks. Access control management systems can combine technologies for increased reliability and convenience.
Keypads and Touchscreens
Keypads and Touchscreens are at the low end of electronic locking systems. The unit replaces the key ...
Keypads and Touchscreens are at the low end of electronic locking systems. The unit replaces the key to a deadbolt or door with a keypad or touch screen. Most units have a back-up physical key. Operating with a basic reader, the user enters a preprogrammed code. Provided the code matches, the system releases the lock. The keypad can accept multiple codes and temporary codes. Touch screens can accept a password, PIN, or biometric, such as a fingerprint.
Biometric Readers
Biometric Readers typically use fingerprints to verify credentials but can use other biometrics such ...
Biometric Readers typically use fingerprints to verify credentials but can use other biometrics such as a palm scan, retina scan, or voice activation. The scanner converts the biometric measure into a numerical template, which serves as credentials. Scanners can approve multiple users and temporary access. The key benefit of biometric readers is the difficulty in faking credentials or bypassing the system. The downside is the higher cost. The original authorization requires the physical presence of the user to present the biometric measure used. It takes more time to initiate a code, and biometric systems have the highest incidence of system failure. For instance, an injury to the index finger could lead to the rejection of an authorized individual because the reader cannot match the print with the one in the system.
Remote Access or Smart Locks
Remote Access or Smart Locks allow the user to control the lock without proximity requirements. Rath ...
Remote Access or Smart Locks allow the user to control the lock without proximity requirements. Rather than being at the location, the locks operate based on software transmitted through Bluetooth, WiFi connections, or Z-wave technologies. Remote access allows the user to lock or unlock doors or drawers from a remote location. The system can also send alarms and updates when a door is locked, unlocked, or open. Users can enter credentials from a smartphone, computer, or tablet. Smart locks allow users to restrict access to only certain times of the day, access to expire, and allows users to change access codes within seconds to grant or deny credentials.
Key Cards, FOB and RFID Readers
Key Cards, FOB, and RFID Readers use a radio transmitter to communicate between the FOB and the cont ...
Key Cards, FOB, and RFID Readers use a radio transmitter to communicate between the FOB and the controller. A keycard, FOB, employee badge, or other programmed card tie credentials to the reader without requiring smart technologies. A reader can accept a swipe, tap, chip, or contactless cards. One FOB can open multiple doors or drawers provided they are part of the same access control system.
Bluetooth
Bluetooth technology is an economical option using similar functionality to Wi-Fi systems without requiring as much battery power to operate. The locks connect directly to a mobile or FOB devices with a Bluetooth receiver. Proximity readers allow authorized personnel to verify credentials and unlock the
door without having to touch the lock. Tapping the smartphone or key FOB on the controller will also grant access. The technology can integrate seamlessly with a smartphone, FOB key card, or other smart device connected with the access control reader. The system does not require a separate communication hub and can sometimes integrate with an existing security system. The downside is that the smartphone or FOB must be close to the reader to operate.
Wi-Fi
Wi-Fi technology has dramatically expanded the use of remote locking systems. Today, users and administrators can control devices from anywhere there is a reliable WiFi connection. The reader communicates with the access control panel through an existing Wi-Fi connection. A Wi-Fi connected lock will record
usage and send alerts based on activity. The software can gather statistics on multiple locks and present the data in an easy to read format, giving administrators more tools for tracking and decisions making.
Z-Wave
Z-Wave technology requires a communication hub to operate all devices connected to the hub. The receiver must be within 100 feet for the reader to accept credentials. Extended reader devices can spread the range to 500 feet. Due to its limitations and capabilities, Z-wave is most often found in residential
settings.
03
Methodology of Access System
Methods of System Communication with Other Security Devices
Methods of System Communication with Other Security Devices
Cloud-Based Access Control Systems
Cloud-Based Access Control Systems store data, credentials, logs, and other information at a remote ...
Cloud-Based Access Control Systems store data, credentials, logs, and other information at a remote site on a remote server through a third party, using cloud-based software. The key benefit of cloud-based communication is the ability to access the account from anywhere there is a secure internet connection. Companies can also coordinate systems from multiple locations and offices.
Smartphone-Based Access Control Systems
Smartphone-Based Access Control Systems use similar technology connecting users through a smartphone ...
Smartphone-Based Access Control Systems use similar technology connecting users through a smartphone app. After downloading the app, an administrator can remotely access the system, make changes, and view stored data. Users may also gain access to the system from the app, which verifies the user’s credentials at the reader. With a smartphone or mobile-based system, the user can log in to the app, hold the phone next to the reader to verify credentials, and enter a secure area without having to carry a badge or keycard.
IoT (Internet of Things) Based Access Control Systems
IoT (Internet of Things) Based Access Control Systems connect the reader to the control panel throug ...
IoT (Internet of Things) Based Access Control Systems connect the reader to the control panel through a dedicated server. The firm’s software controls the functionality of the system with users able to gain access through internet-based protocols.
The Methodology of Access Control Systems
There are common methods access control systems communicate with other security devices. These systems connect between the reader and server using cloud-based, smartphone-based, or IoT Based Access Control Systems.
Authorization
The process of deciding and assigning who gets clearance to what. Authorization turns outsiders into affiliates based on the access control method used (RBAC, DAC, or MAC).
Typically, company policies determine who can enter what areas, which positions receive what clearances, and whether various team members share access. Each employee category receives a list of clearance levels assigned, making it easier for managers and administrators to initiate and terminate access based on the duties and responsibilities of the employee or position. Administrators then assign credentials based on the privileges allowed.
Management
The process of controlling who has access to which secure areas. The administrator manages authorization based on company protocols, which can include activating and canceling
credentials, monitoring access through internal tracking, and troubleshooting issues. A manager may remotely issue, cancel, or reset a code, controlling what members of the team will have access to any given area. They can also access a record of entry and exit to an area, provided the system records an audit trail.
Authentication
The process of accepting or rejecting a set of presented credentials. Authentication validates the associate approval level, confirms access credentials based on a preapproved list,
and verifies the authorization of any given individual. The employee or affiliate presents credentials to a reader, which then verifies those credentials to determine if the system will grant entry. The three most common factors used to authenticate a user include:
- Information, the user, knows or selects such as a password, phrase or PIN
- Something the user carries such as a key FOB, key card, or smart card
- Something the user is such as biometric measures like a fingerprint, palm print, or eye scans
Audit
The process of monitoring access to secure areas. An audit trail provides details of entry and exits as well as credential rejections. A review of the data can improve security by
identifying areas for improvement, recognize unusual behavior, reduce incidents of internal theft, help investigate suspicious events, improve recordkeeping, and meet compliance requirements.
Access
The process of either unlocking a door to a secure area or triggering an alarm. When presented credentials match the authorization list, the door unlocks, and the member gains entry
to the secure area. When credentials do not match the area, door, or drawer remains locked. A keyless lock with an audit feature will log both acceptances and rejections. Some systems will initiate additional security measures, such as cameras, in the event of a rejection.
04
Features and Benefits
Key Features and Benefits of Using an Electronic Access Control System
Key Features and Benefits of Using an Electronic Access Control System
Security Risks to Mitigate with Access Control Systems
Tailgating
Tailgating occurs when an authorized person gives an unauthorized person access and is the most comm ...
Tailgating occurs when an authorized person gives an unauthorized person access and is the most common security breach. For example, an individual with clearance could hold the door for an unauthorized person, share their credentials, or give someone without clearance access to files, records, or assets contained in secure doors or drawers. Employee training is the most effective way to combat this vulnerability. Other measures to mitigate the risk of tailgating include using security cameras, multi-factor authorization, or requiring duel authentication.
Door Ajar
Door ajar or left open is another form of a security breach. Thieves can spoof a magnetic locking sy ...
Door ajar or left open is another form of a security breach. Thieves can spoof a magnetic locking system with a strong magnet set in place of the magnetic strike position, tricking the system into believing it is secure when it is not. Thieves can also manipulate a magnetic lock by cutting the power to the system, which unlocks the door, leaving it unsecured. Mitigate the risk with a battery-powered back-up on magnetic locks or using electronic strike locks. Other measures to mitigate the risk of unlocked doors could include installing a system with an auto-close and auto relocking feature or putting an alarm on the door, which will notify management when a door does not close and relock properly.
Natural Disasters and Power Failures
Natural disasters and power failures can create a security breach when utilizing magnetic locking sy ...
Natural disasters and power failures can create a security breach when utilizing magnetic locking systems. Choosing electronic strike locks will prevent lock failure during a power outage, making them better suited for areas requiring high levels of security.
Computer Equipment Failure or Cyber-Attacks
Computer equipment failure or cyber-attacks occur when a computer crashes, or a hacker gains unautho ...
Computer equipment failure or cyber-attacks occur when a computer crashes, or a hacker gains unauthorized access to a system. Mitigate the risk by employing cybersecurity measures, frequently backup files, and maintain updated software. Managers can program intelligent readers to operate independently of the main controller, which will allow physical access to a secure area even if the computer system or main controller is compromised. Separating the security system from the primary business systems is another way to ensure a cyber-attack does not leak security credentials for physically secure areas.
Access Card Failures
Access card failures. Access cards can become vulnerable if lost and not reported. In some cases, po ...
Access card failures. Access cards can become vulnerable if lost and not reported. In some cases, portable readers can compromise access cards giving an unauthorized person the credentials to access a secure area. To mitigate the risk, use a system that encrypts the transmission from the proximity reader to the access control panel, and immediately change credential codes for terminated employees or lost access cards. Other measures to mitigate the risk of access card failure might include completing system software updates immediately, requiring duel authentication, multi-factor authorization, or activating security cameras.
Sequential Authorization Codes
Sequential authorization codes. Producing new codes in sequential order will create a system vulnera ...
Sequential authorization codes. Producing new codes in sequential order will create a system vulnerability because someone with pervious access can “count up” to obtain a new and valid access code in the system. To mitigate this risk, always issue codes in random order to produce unique and non-sequential access credentials.
Mechanical Keys
Mechanical keys. Many access control systems provide physical keys for use in the event of system fa ...
Mechanical keys. Many access control systems provide physical keys for use in the event of system failure. These physical keys create a vulnerability because of the ease of key duplication and the inability to track and manage physical keys.
05 Choosing and Access Control Systems

Types of Access Control Systems
Companies must also determine which employees have access to what areas. To decide which paradigm to use, a company will look at its corporate structure, employee roles, and security needs. Employees typically fall into one of four categories: Basic, Observer, Manager, and Administrator.
Basic Security Clearance
Includes access to secure spaces
Observer Clearance
Observer Clearance grants access at the basic level, plus the ability to view the logs of who entered and exited secure spaces.
Administrator Clearance
Administrator Clearance decides who can have access to where along with the ability to see tracking logs.
In addition to dividing employees into roles, administrators must decide which employees will gain access to which secure areas. The most common methods to make these decisions include role-based, discretionary access, or mandatory access.

How to Choose an Access Control System
Technology is rapidly changing the physical security landscape. Installing an access control system can increase the level of security attained as well as providing tracking tools to monitor access to secure areas. A top consideration of any security system is the level of security offered, but it is not the only one. Other important factors might include the quality of the hardware, ease of updating the software to reduce vulnerability to hackers, and the encryption of credentials. The systems can operate as a standalone device or integrated within an existing system. The ease of changing user credentials, user experience, use of multifactor authentication, and level of administrative control can narrow down the system selection.
Here are a few of the top areas to consider when choosing an electronic access control system:
Application Needs
The first step is to evaluate the need for access control. Where will the system be installed and what level of security is required for that area. Who will need access and during what hours? The application will determine the features required.
Consider entry doors, storage, or IT rooms, along with desks, file cabinets, or other doors and drawers holding secure information, valuable assets, or expensive systems. Sensitive information might include client, company, or vendor data and assets.
Security Needs
What level of security does the area require? Will single authorization suffice or does security concerns require multi-factor authorization? How many users will need credentials? What level of monitoring will maintain security?
Compliance and Regulatory Requirements
What regulatory arms monitor the security measures the company chooses? Does meeting compliance requirements include regular reports? What policies and procedures must coordinate with the security measures implemented?
Installation Requirements
How will the company install the system? Will the new system integrate with existing security protocols or operate as a standalone access control system? Will management use in-house staff to install the system or is professional installation needed? How many locks will the control panel operate? What are the company’s software integration needs? Is the system compatible with third-party hardware?
Compatibility with Existing Security
Can the system integrate new protocols with the current system. New systems may require all new locking devices or could utilize the existing hardware. Is the new system compatible with other security components such as surveillance cameras?
Communication
How will the new system communicate with existing technology within the company? How will user key cards communicate with the reader to verify credentials? What type of authentication will the system support?
Expandability
Will the system grow with the company? Can it expand and upgrade as the company grows and technology changes?
Ease of Use
How easy is it for managers or administrators to configure and maintain the software? Can they overcome technical issues, cancel, and reissue entrance credentials, and monitor the activity in the secure area? Also consider the ease of use for everyday users, which could include individuals, employees, subcontractors, or customers. The user experience will factor into the effectiveness of the security system. Security measures users find it difficult to maneuver can encourage shortcuts and actions taken to bypass protocols, which can compromise the system.
Customer Support
Choose a company which offers a professional level of customer support during the sales, installation, and implementation phase. The company should also have a customer service team in place to assist management with questions or troubleshooting during the operation of the system.
Cost
Cost how much will the access control system cost to purchase, install, and maintain over the next decade.
Implementation

Create a Plan
Any new security system should begin with a risk assessment. What areas are vulnerable to a security breach? What level of security can reduce or eliminate that vulnerability? Will the solution integrate into existing security systems?
Staff Training
Staff education will increase the effectiveness of any new security measures. Training should include not only new policies and procedures, but an understanding of the importance of adding this additional layer of security.
“With high-security card access systems, one of the most important things is that the end-user is properly trained and knows how to update their database so they can take out on a moment’s notice a card of an employee that has been terminated… The bottom line is, a high-security system is only as good as the people operating it because if they’re not in high-security mode, it will not stay at that level.” ⁷
Conduct Regular Checks
Security checks can include ongoing staff training, log reviews, and tracking measures that audit the effectiveness of the system. A critical review of audit data on an ongoing basis can uncover new problems, highlight vulnerabilities, and uncover new areas that need additional security.

Conclusion
Electronic access control systems provide a new level of physical security for small and large businesses. New technologies have improved access control systems, making them intuitive and responsive to business needs, transforming the physical security of millions of offices. Electronic access control systems secure areas from parking garages, buildings, down to cabinet-level security of file cabinets and desk drawers. Utilizing the newest technologies creates a management system that will help maintain a safe environment for employees and visitors, reduce losses due to security breaches, and identify system vulnerabilities to better protect the company and the assets and data it maintains.
We’re here to help you enhance your security!
Get in touch with our expert team today for a quote!




